The people we serve depend on us to give our very best effort to secure and protect their private information.
It becomes increasingly clear that the bad guys are here to stay and they’re focused on finding ways to steal our information. They’re well-funded and bright and it’s up to technology professionals to stand in the gap to protect our information.
If we take these threats seriously then we can make a few assumptions right off of the bat.
- Our systems are more vulnerable than we think.
- The only way we can dedicate the time and energy necessary to protect our systems and data is to realize we’re a target.
- Our adversaries are active, well-funded and are deliberately looking for ways to steal our information.
- They’re sophisticated and are smarter than most of us in finding security gaps.
- Our employees aren’t focused on security, thus they’ll be lackadaisical about the security measures we implement.
- Accidents will happen that inadvertently expose our systems and data to vulnerabilities.
- The security investments we’ve made in the past are in the past. The bad guys have made their adjustments and are proceeding accordingly.
The information security risks we face today will continue to evolve and expand so we’re faced with the question of what can we do to protect ourselves?
The only effective way we can meet the challenge is to center ourselves and focus all of our attention on what we can control and leave the rest to the press.
Our most formidable enemy is really our own complacency. If we ever let our guard down and assume that we’ve got it all under control, we’ve opened ourselves up for a fall. We can address complacency with focus and purpose. Diligence along with a knowledgeable approach is the strongest ally we have.
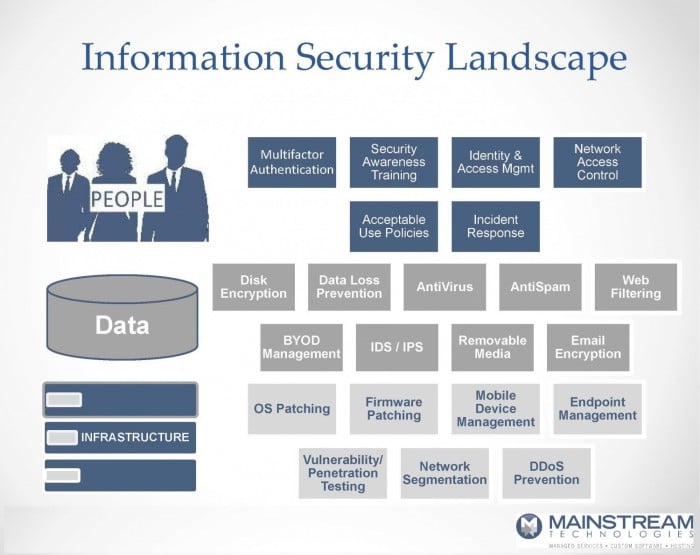
The Information Security Landscape
The information security landscape can be generally broken down into three components; People, Data, and Infrastructure. Each of them must be addressed independently because a lapse or gap in any one of them will affect the other two.
An annual information security (IS) assessment (some people use the term cyber security) is essential for creating a roadmap to address the security needs of your business. The IS assessment is designed to identify what security controls are in place and if they’re aligned with the associated risk of exposure. It will establish a baseline so an organization can knowledgeably plan for and address the gaps with policy, procedures or additional tools as required.
If you would like to take the first step in seeing how your security measures stack up, take a minute to complete a seven-question assessment by clicking here. By no means is it intended to be a comprehensive assessment, but it may raise some questions that you haven’t thought of before.