Every small business is vulnerable to cyber-attacks from literally everywhere in the world.
Many of us think that we are too small to be targeted, but nothing could be further from the truth. We are all at risk. We all have data that is valuable to us and we rely on technology that can actually be used as an attack vector. The bad actors know this, and if they succeed in locking up our systems, we will pay handsomely for their restoration. Small businesses are especially vulnerable because we have traditionally underestimated the risk, and the associated costs if we are victimized.
There is some good news, however. If we choose to ramp up our defenses, we can take some simple steps to improve our protection. Some are basic, while others are more involved, but together, they all contribute to a layered defensive foundation between our data and the bad actors. An attack may get past one layer, but the odds are in our favor that they can’t get through them all.
A layered cybersecurity strategy maximizes protection while keeping costs under control.
Layered Cybersecurity Roadmap
No single tool or policy can adequately defend against every type of attack. A variety of tools and approaches are necessary for an adequate defense. Since there are so many tools out there, it is easy to buy ones we don’t need or underutilize the ones we do have.
The first step is to have your IT partner execute a cybersecurity assessment. This assessment will provide an accurate snapshot of your existing defenses. Once you know where you are, you can put a plan together to add layers that will yield the biggest bang for the buck. For example, workforce awareness training or multi-factor authentication are both very affordable and have been proven to be very effective.
Knowing the function and role of each potential tool is essential for a cost-effective and comprehensive cybersecurity layered defense.
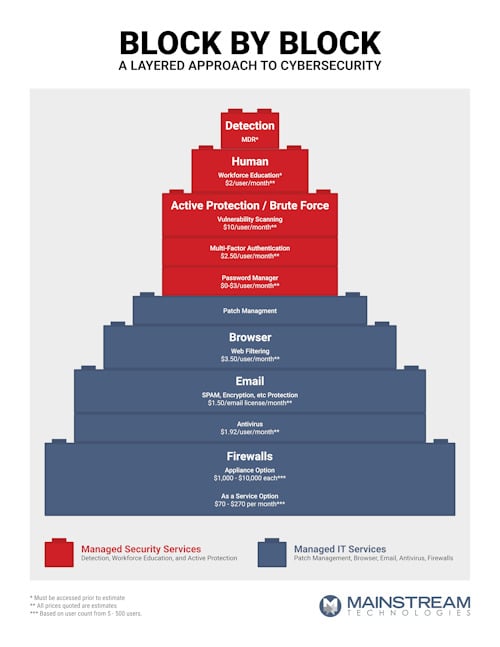
Layered Cybersecurity Strategy Tools
- Level 1
- Firewalls – keeps out the bad stuff
- Email Protection – SPAM, Encryption, etc
- Browsing Protection to keep users from going to bad web sites
- Patch Management to assure software is current
- Level 2
- Active Protection
- Multi-factor Authentication
- Password Manager
- Vulnerability Scanning
- Active Protection
- Level 3
Summary
Since small business is vulnerable to cyber-attacks, we should take these threats seriously to protect our businesses and those who depend on us. Securing our technology requires a roadmap to direct and measure our efforts knowledgably. Once a plan is in place, there are some very affordable tools that can significantly reduce the risk. If you’re not sure how to proceed there are many IT service firms out there who want to help. You’re not alone at any point in the process.
ABOUT MAINSTREAM TECHNOLOGIES
Mainstream Technologies is a Little Rock, AR IT service company. We offer managed technology services, data center services, custom software development, and cybersecurity services. For more information, please contact Jeff Pracht at this link.





