Every organization uses technology and is under cyber-attack from literally everywhere in the world. This isn’t going to change anytime soon. A layered cybersecurity strategy can help combat these attacks, maximize protection, and keep costs under control.
What we need to understand is that no single tool or policy can adequately defend against every type of cyber-attack. A variety of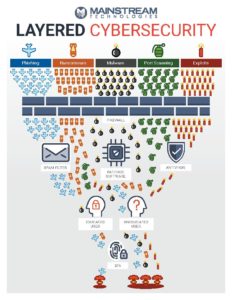
Knowing the function and role of each potential tool is essential for a cost-effective and comprehensive cybersecurity strategy.
Layered Cybersecurity Strategy Tools
- Firewalls
- Designed to keep the bad stuff out
- Cost Range – Firewall as a Service – $70-$270 month
- Email Protection – SPAM, Encryption, etc
- Spam Filter, Encryption, etc
- Cost Range – $1.50~ per address per month
- Browsing Protection to keep users from going to bad websites
- Cost Range – $3.50/device/month
- Brute Force Protection – Once the bad guy targets you
- Multi-factor Authentication
- Cost Range – $2.50/user/month
- Password Manager
- Cost Range – $0-$3/user/month
- Vulnerability Scanning
- Cost Range – $10/user/month
- Human
- Workforce Education
- Cost Range – $2.50/user/month
- Detection
- SIEM, FIM
- Cost Range – Call for pricing
- Multi-factor Authentication
Resources:
Block by Block: A Layered Approach to Cybersecurity – Live Event Recording
If you would like more information about how to improve your cybersecurity protection, please send Sara an email, by clicking this link.





